Welcome to a world where the letters ‘IBM’ signify innovation and ironclad security.
Let us get started as….,
Today, we delve into the realm of data encryption within IBM i applications.
In this guide, you will learn:
- What is data encryption?
- Why do we need encryption?
- Using encryption in the IBM i System
- Advantages and disadvantages of encryption
What Is Encryption
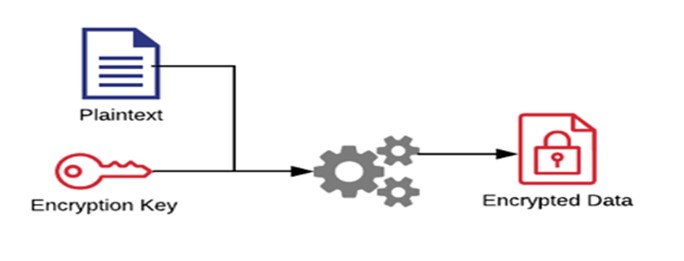
Encryption involves securing and protecting data and information using mathematical models, algorithms, and techniques so that only those with the keys can access it. There are a variety of encryption processes and techniques, ranging from simple to overly complex.
Encryption performs four essential functions:
- Confidentiality: keeps the contents of the data secret.
- Integrity: verifies the origin of the message or data.
- Authentication: validates that the content of the message or data has not been altered since it was sent.
- Non-repudiation: prevents the sender of the data or message from denying they were the origin.
Why Do We Need Encryption
Our daily life is filled with encryption, whether we know it or not. Data encryption is important because it helps protect people’s privacy and secures data from attackers and hackers who intend to harm or misuse it, causing financial losses to individuals or organizations. Additionally, they can misuse it for corporate espionage, Political espionage, Hacktivism, Revenge, Notoriety, etc. In the 21st century, encryption is a valuable tool to ensure cybersecurity.
To keep data and systems protected, businesses need encryption. In terms of protecting valuable information from malicious individuals, it is one of the most effective tools available. Even if the attacker manages to access system data, these methods prevent them from viewing, reading, or manipulating it. With no encryption keys, the data will remain unreadable.
Types Of Encryptions
Data encryption comes in two forms: in-transit encryption and at-rest encryption.
1. Encryption At Rest
The term encryption at rest refers to a type of encryption for data stored or “at rest” in a device or system, such as a hard drive, database, or cloud storage. Using this encryption technique ensures that data is safe from theft and unauthorized access, even if the system or device is physically compromised.
We can use Db2 native encryption to encrypt our databases and backup images.
We can use IBM® InfoSphere® Guardium® Data Encryption to encrypt the underlying operating system data and backup files.
Encrypted File System (EFS) can encrypt operating system data and backup files. Use EFS if we are running a Db2 system on the AIX® operating system, and we are interested in file-level encryption only.
2. Encryption In Transit
It is the process of encrypting data while it is being transported over a network between two devices or systems. This technique safeguards data against theft and unauthorized access using an encryption technique while it is being transported.
To achieve the best results, we should also encrypt data in transit as well as at rest. Encryption only on the disk, but not the network, can cause problems. A hacker would be able to hang out in the network traffic to help them gain access to our disk. In turn, our data would undoubtedly be in hot water. As far as data encryption is concerned, having the entire range covered will give us peace of mind.
For data encryption during transit between clients and DB2 databases, we use Transport Layer Security (TLS).
Types Of Encryption Algorithms
The two most common types of encryption algorithms are symmetric and asymmetric.
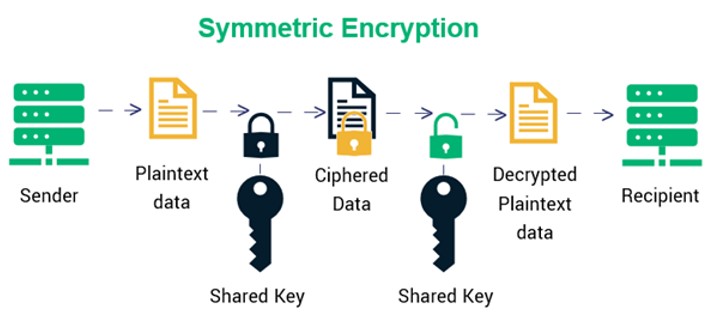
1. Symmetric Encryption
This algorithm uses the same key for both encryption and decryption and is also called a shared key algorithm or private key algorithm. Encryption and decryption of symmetric key ciphers do not require as much computer power, meaning there is less delay in decoding the data.
The disadvantage is that an unauthorized person can decrypt data and messages sent between parties if they have the key. As such, the transfer of the shared key needs to be encrypted with a different cryptographic key, leading to a cycle of dependency.
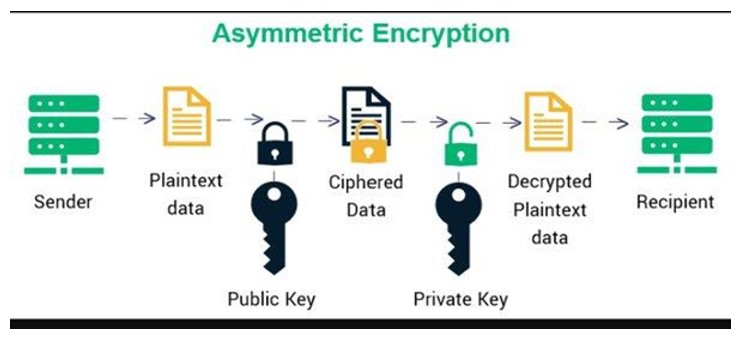
2. Asymmetric Encryption
The encryption and decryption of data are performed using two separate keys, also called public-key cryptography. The public key is shared among all parties for encryption. Anyone with the public key can then send an encrypted message, but only the holders of the second, private key can decrypt the message.
Since asymmetric encryption uses a large public encryption key, often 1,024 to 2,048 bits, it is more expensive to produce and more computationally demanding to decrypt. Due to this, asymmetric encryption is often not suited for large data packets.
Use Of Encryption in IBM i Applications
Db2 Native Encryption
DB Database backup images and key database files stored on external storage media can be protected from inappropriate access by native encryption.
It uses a two-tier approach to data encryption where data is encrypted with a Data Encryption Key (DEK), which is in turn encrypted with a Master Key (MK). The encrypted DEK is stored with the data while the MK is stored in a keystore external to Db2.
Db2 native encryption ensures that the DEK is never exposed outside of the encrypted database, transaction log, or backup file. There are no interfaces provided to access the DEK in either its clear text or encrypted forms. As the MK is stored in a different location from the encrypted data, the chance of the encrypted DEK being concurrently exposed with the MK used to encrypt it is very unlikely. Since the risk of the DEK being exposed is extremely low, the need to rotate it is negligible. The rotation of the MK, which is used to protect the DEK, can be done efficiently without the need to decrypt and re-encrypt the data.
To use encryption on the system, one must purchase an encryption license, upload certificates, activate the license on the system, set up the key management method, and create copies of the keys.
The system supports optional encryption of data at rest. This support protects against the potential exposure of sensitive user data and user metadata that is stored on discarded, lost, or stolen storage devices. In addition, the system supports automatic locks of encrypted drives when the system or drive is powered down. We need a master key to unlock the drive and continue I/O operations when our system is encrypted and restarts. The master key is created when we enable encryption on the system.
AS400 Encryption, Masking, and Scrambling Features for IBMi DB2 Database encryption algorithm can be used to encrypt both numeric and alphanumeric fields in DB2 database using one of the following: AES256, AES192, AES128, TDES24, TDES16, TDES8, DES.
Unauthorized users will not be able to see the encrypted data, regardless of where the data is stored or how it is accessed. Uses universally accepted PCI-approved encryption algorithm standards.
Field Security
It prevents the updating of fields while allowing read access unrestricted.
Masking
It replaces all or selected positions of a field on the fly, before displaying the data to the requester. The field is masked only at the time of the record read, and the actual DB2 field remains unchanged.
Scrambling
It applies an arithmetic function on all or specified positions of a field on the fly, before displaying the data to the requester. Changes to fields take place at the time of the record read, and the DB2 field remains unchanged.
Full or partial masks of fields can be applied to any kind of database field. For numeric fields, we have the option to scramble data, which is ideal for data used in development and testing applications.
RCAC Field Masking
It is used to perform field masking using the Row Column Access Control feature available in OS400 V7R3 or later.
IFS File Encryption
This feature is used for encrypting any object in the IFS.
Save File Encryption
It replaces a SAVF object with an encrypted file and cannot be used on any system until the save file is unencrypted. Good for encrypting files for backup.
Key Management
It provides two-tier encryption requiring master keys to generate data keys, ensuring strict separation between those who generate keys and those who use them, and keys can also be encrypted. Encryption keys can be stored on an IBM iSeries or a remote server. Encryption keys are assigned to users or groups of users based on roles defined by the administrator. Encryption key strings (characters used by algorithm) can be entered manually or be randomly generated so that even the administrator does not know the encryption key.
User and Group defined Access
It allows for decrypting data for groups of users, without the need for application-level detail.
High Availability Compatibility
Encryption works in high-availability environments without any extraordinary measures being taken. Backups and replicated databases will be identical to the production system and will contain the master and data keys needed to encrypt and decrypt the data.
Back-Up Encryption
Object encryption for backups provides the ability to encrypt and save entire libraries as well as individual objects. Backup processes can be easily integrated with object encryption using a series of commands. Organizations backing their data up to tape, now have an effortless way to make sure the data cannot be read by anyone who is not authorized in case their tapes end up in the wrong hands.
Data Protection
Data encryption adds an important layer of security to an organization’s sensitive information. It offers GUI-Managed File and Field Level Security, making it impossible even for Power Users to access restricted fields.
Application Independence
Field Encryption has been engineered to minimize the impact on mission-critical applications that could be affected by encrypting and decrypting processes. Existing database file structures remain unchanged. Organizations will typically not require any program changes.
Compliance
Requirements such as the PCI Data Security Standard (requirement 3) specify the protection of stored cardholder data. Enterprise Security provides the ultimate answer to that requirement by a foolproof encryption and decryption mechanism using universally accepted PCI-approved encryption algorithm standards.
Reports
With the existing features provided by the Enterprise Security product including Exit Point Management, Object Authority Management, and IP Packet Filtering, enforced offers the ultimate tool for data protection.
Advantages Of Encryption
1. Protects Data Across Devices
The movement of data is constant, whether it is messages between friends or financial transactions. Encryption paired with other security functions like authentication can help keep data safe when it moves between devices or servers.
2. Ensures Data Integrity
In addition to keeping unauthorized people from seeing the plaintext of data, encryption safeguards the data so that malicious actors cannot use it to commit fraud extortion, or change important documents.
3. Protects Digital Transformations
With more organizations and individuals using cloud storage, encryption plays a key role in protecting that data while it is in transit to the cloud, once it is at rest on the server, and while workloads are processing it. Google offers different levels of encryption, as well as key management services.
Disadvantages Of Encryption
1. Ransomware
While encryption is used to protect data, malicious actors can sometimes use it to hold data hostage. If an organization is breached and its data accessed, the actors can encrypt it and hold it ransom until the organization pays to have it released.
Conclusion
It has never been more critical for organizations that store sensitive structured data or personally identifiable information, such as credit card numbers, social security numbers, birth dates, addresses, or account numbers, to protect themselves from security breaches. A breach of high-value data can be prevented by encrypting the information while ensuring compliance with various government and industry regulations. A breach of high-value data can be prevented by encrypting the information while ensuring compliance with various government and industry regulations. However, traditional database encryption solutions often require changes to the database table format and can slow performance. Enterprises need a solution that secures sensitive data that is critical to their business operations without costly and time-consuming investments.